Cadence of Hyrule Review

Official Score
Overall - 90%
90%
If you are a Zelda fan, then Cadence of Hyrule should be a no-brainer. For anyone who likes great music, fun gameplay, and action RPGs, this one is for you.
Cadence of Hyrule mixes Crypt of the NecroDancer and Zelda into a unique rhythm-based roguelike. Is it a match made in heaven, or should you stick to the more traditional Zelda entries? Check out our review and find out.
Cadence of Hyrule Review
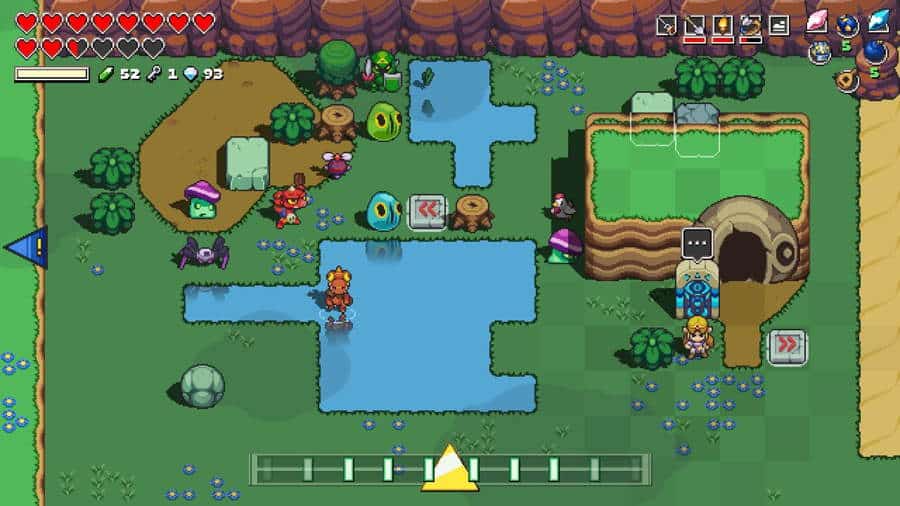
Booting up the game for the first time, players will take on the role of Cadence, a confused young woman trapped in Hyrule. After a brief tutorial, players will be able to choose between Link or Zelda. Link has a more straightforward approach to play, with the ability to hold his shield up longer and deflect enemies attacks easier. Zelda, on the other hand, has magic at her disposal, and can manually control where her fireball goes. This makes her powerful, but also more challenging to play. After you choose, you are thrust into this games version of Hyrule and tasked with clearing four dungeons to gain access to Hyrule Castle. However, this is far easier said than done.
For those unfamiliar with the roguelike genre, expect to die – a lot. The first hour or two will no doubt be spent trying to learn the games rhythm-based combat and memorizing enemy patterns. You also lose certain items and Rupees when you die. If this sounds overwhelming already, don’t worry, it is just a lot of one-two one-two on the D-Pad. The rhythm part of the combat can be turned off as well, though I didn’t get nearly as much enjoyment this way. When all was said and done, I had 36 deaths total and a little over nine hours of play time.

Let’s get into how the actual game works. Moving to the beat, you will go one square at a time until you run into an enemy. If you move towards the enemy during the beat, you will attack them with your equipped weapon. For basic enemies, just running straight at them works. However, they will eventually have shields and armor, so you’ll need to move around them a bit more. As far as enemies are concerned, you get a lot of Zelda classics. The knights from Link to the Past, Chu Chus, Poes, Deku Scrubs, Bokoblins, and Lynels all make the rounds, to name a few.
While your main task is to clear the dungeons, the land of Hyrule is full of other places to explore. Kakariko Village and Gerudo Valley have Bombchu bowling and archery contests. The Lost Woods lures in wayward travelers in and tosses them right back out unless they know the right path. Cracked walls are waiting for you to throw a bomb at them, revealing their secrets and hidden merchants. Fortune tellers are waiting to take your hard-earned Rupees to help point you in the right direction. And, of course, the great fairies are waiting to be found, so our weary heroes can heal up and relax.
While we are talking about Rupees, let’s go over the two currencies in the game. Zelda’s traditional Rupees are earned by beating enemies, looting chests, and digging through bushes. You can spend these on various items, potions, and some equipment upgrades. When you die, you lose all Rupees, so there is no sense in hoarding them. Diamonds are the second currency, and these prove to be more important early on. They are used to buy things at the Death store, upgrade weapons, and occasionally trade with certain merchants for special gear. You do not lose these when you die, and they are earned by clearing a whole room of enemies. They are harder to get, but also more valuable in the beginning.
Cadence of Hyrule allows you to use a number of different weapons on each character, but no one can use all weapon types. For instance, Zelda and Cadence can use a dagger, but Link cannot. You start with one weapon on your character and have to find the rest. You can then use your diamonds to upgrade most weapons with special effects like poison or extra damage. The weapons also have different attack types; a spear has a greater reach, but a broadsword can hit multiple enemies at once. I was impressed by the amount of weapon options you are given on most characters. That said, there is no hammer, and that is a crying shame.
My chief complaint about the game come from how easy it eventually gets. There was a point where I just felt in tune with the game and didn’t die for close to five hours, steamrolling all dungeons. I thought the dungeons were well put together, but the lack of challenge left me a bit disappointed. In addition, you eventually run out of things to buy with both Rupees and Diamonds. I wanted to go back and play more after I beat it, but outside of starting a new game, I didn’t see any reason to. That doesn’t take away from the fun I had playing it; I just wanted more.
So the big question left is: How is the music? The answer: fantastic. When I started with Link, I went over a beach square, and the music hit me like a brick. The overworld theme has Tal Tal Heights, Hyrule Field, and The Great Sea all on one track. That might sound like a mess, but as soon as I heard it, all I wanted to do was explore. This whole game is just one awesome remixed song into another. Its a massive play on nostalgia, yes, but it works wonders. Special shoutout to the Windmill Hut Song of Storms remix.
If you are a Zelda fan, then Cadence of Hyrule should be a no-brainer. For anyone who likes great music, fun gameplay, and action RPGs, this one is for you.



